Setting up a Prometheus monitoring stack in Kubernetes, utilising helm. | by Craig Godden-Payne | Nov, 2020 | Medium
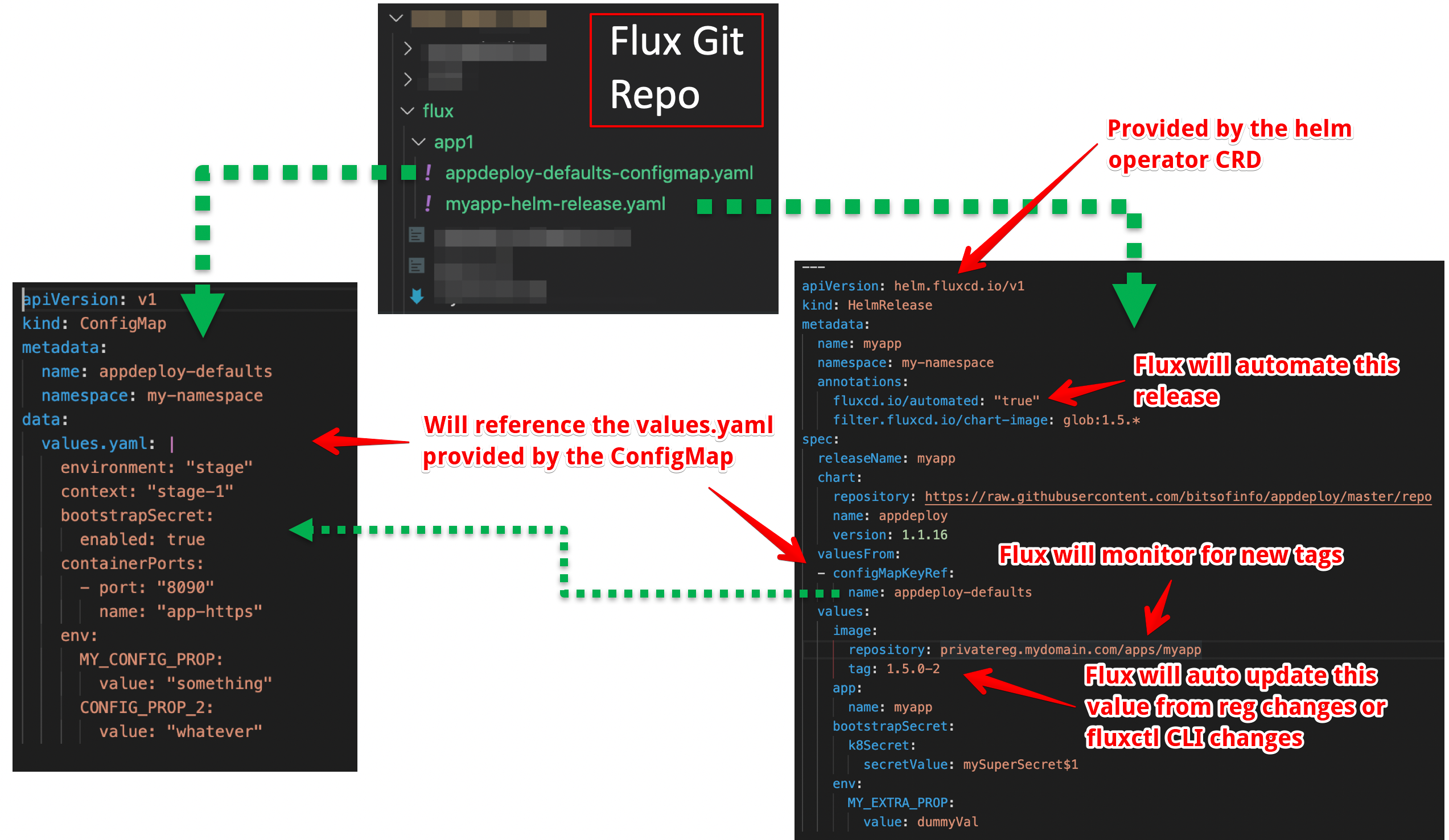
Continuous delivery with Flux. The acronym “CI/CD” and its respective… | by bitsofinfo | Level Up Coding

Kustomize: Kubernetes configuration management, the easy way - Pieter Vincken — Ordina JWorks Tech Blog






![Kubernetes] Helm 사용법 Kubernetes] Helm 사용법](https://img1.daumcdn.net/thumb/R800x0/?scode=mtistory2&fname=https%3A%2F%2Ft1.daumcdn.net%2Fcfile%2Ftistory%2F990C3B4C5C3E1CA502)